Information on the ransomware group LYNX for clients. (INFORMAL FINDINGS)
ALIAS NAMES???
Julio – Jaime Vazquez possible email julioyjesus818@gmail
Age: 43
601 riverside ave
Lyndhurst NJ 07071
DOB- Nov 1981
Potential land line 212-222-6438
NJ Puerto Rico, Williamsburg or providence forge Virgina
466 E 35 apt 1 2016-2017
lynxstorage1.net
- Updated 14 hours ago – EMAIL WAS CHANGED TO email@gmail from other<<
- Domain Information
- Domain:lynxstorage1.net
- Registrar:REGISTRAR OF DOMAIN NAMES REG.RU LLC
- Registered On:2024-07-26
- Expires On:2025-07-26
- Updated On:2024-07-26
- Status:clientTransferProhibited
- Name Servers:a.dnspod.com
- c.dnspod.com
- Registrant Contact
- Name: Julio Dzheim
- Organization: Private Person
- Street: 466 E 35th ST
- City: Paterson
- State: indiana
- Postal Code: 07504
- Country: US
- Phone: +1.9739289242
- Fax: +1.9739289242
- Email: [email protected]
- Administrative Contact
- Name: Julio Dzheim
- Organization: Private Person
- Street: 466 E 35th ST
- City: Paterson
- State: indiana
- Postal Code: 07504
- Country: US
- Phone:
- +1.9739289242
- Fax: +1.9739289242
- Email: [email protected]
- Technical Contact Name: Julio Dzheim
- Organization: Private Person
- Street: 466 E 35th ST
- City: Paterson
- State: indiana
- Postal Code: 07504
- Country: US
- Phone: +1.9739289242
- Fax: +1.9739289242
- Email:
- [email protected]
Domain Name: LYNXBLOG.NET
Registry Domain ID: 2900253374_DOMAIN_NET-VRSN
Registrar WHOIS Server: whois.reg.com
Registrar URL: https://www.reg.com
Updated Date: 0001-01-01T00:00:00Z
Creation Date: 2024-07-18T12:49:01Z
Registrar Registration Expiration Date: 2025-07-18T12:49:01Z
Registrar: Registrar of Domain Names REG.RU LLC
Registrar IANA ID: 1606
Registrar Abuse Contact Email: [email protected]
Registrar Abuse Contact Phone: +7.4955801111
Domain Status: clientTransferProhibited https://icann.org/epp#clientTransferProhibited
Registry Registrant ID: wqw5fgknts84lejv
Registrant Name: Julio Dzheim
Registrant Organization: Private Person
Registrant Street: 466 E 35th ST
Registrant City: Paterson
Registrant State/Province: indiana
Registrant Postal Code: 07504
Registrant Country: US
Registrant Phone: +1.9739289242
Registrant Phone Ext:
Registrant Fax: +1.9739289242
Registrant Fax Ext:
Registrant Email: [email protected]
Registry Admin ID: b4v1kv6cfb6vy9ou
Admin Name: Julio Dzheim
Admin Organization: Private Person
Admin Street: 466 E 35th ST
Admin City: Paterson
Admin State/Province: indiana
Admin Postal Code: 07504
Admin Country: US
Admin Phone: +1.9739289242
Admin Phone Ext:
Admin Fax: +1.9739289242
Admin Fax Ext:
Admin Email: [email protected]
Registry Tech ID: ryunwmb-e5ove118
Tech Name: Julio Dzheim
Tech Organization: Private Person
Tech Street: 466 E 35th ST
Tech City: Paterson
Tech State/Province: indiana
Tech Postal Code: 07504
Tech Country: US
Tech Phone: +1.9739289242
Tech Phone Ext:
Tech Fax: +1.9739289242
Tech Fax Ext:
Tech Email: [email protected]
Name Server: a.dnspod.com
Name Server: c.dnspod.com
DNSSEC: unsigned
URL of the ICANN WHOIS Data Problem Reporting System: http://wdprs.internic.net/
For more information on Whois status codes, please visit: https://icann.org/epp
Last update of WHOIS database: 2024.11.13T12:05:37Z <<<
- Likely INFECTION POINT (one of several methods) This would not typically pop in a Browser hidden and has payloads that use Direct links that bypass the mainpage “flagged” URL! DO NOT HIT THIS SITE UNLESS SANDBOXED!
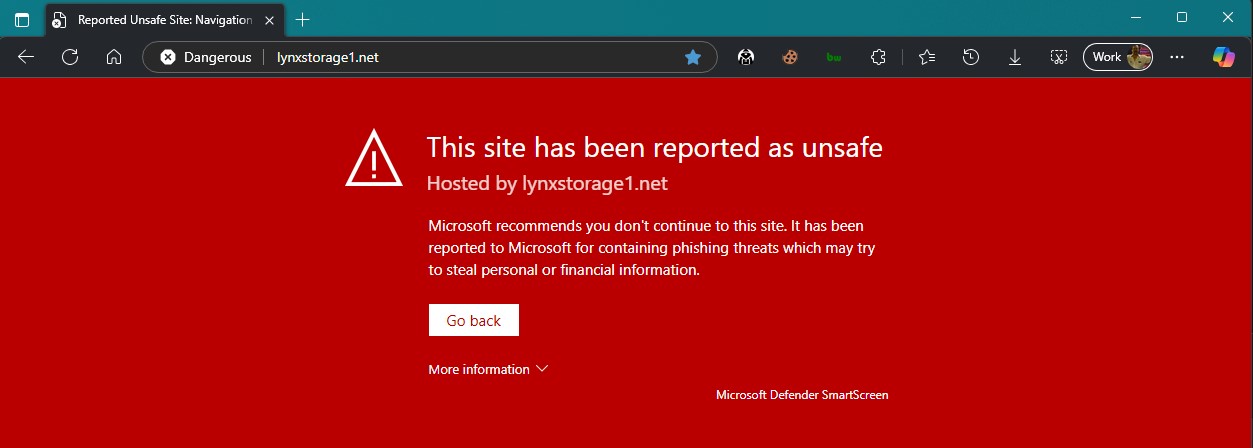
- Lynx on the Prowl: Targeting SMBs with Double-Extortion Tactics Blackberry
- Lynx Ransomware: Rebranding of INC Ransomware – Cyber Security News Aggregator
- Lynx Ransomware Strikes New Targets Unveiling Advanced Encryption Techniques
- In-Depth Analysis of Lynx Ransomware – Nextron Systems
- Lynx Ransomware: A Rebranding of INC Ransomware
- https://unit42.paloaltonetworks.com/inc-ransomware-rebrand-to-lynx/
- Ransomware Groups Demystified: Lynx Ransomware | Rapid7 Blog (updated Sept 12, 2024.
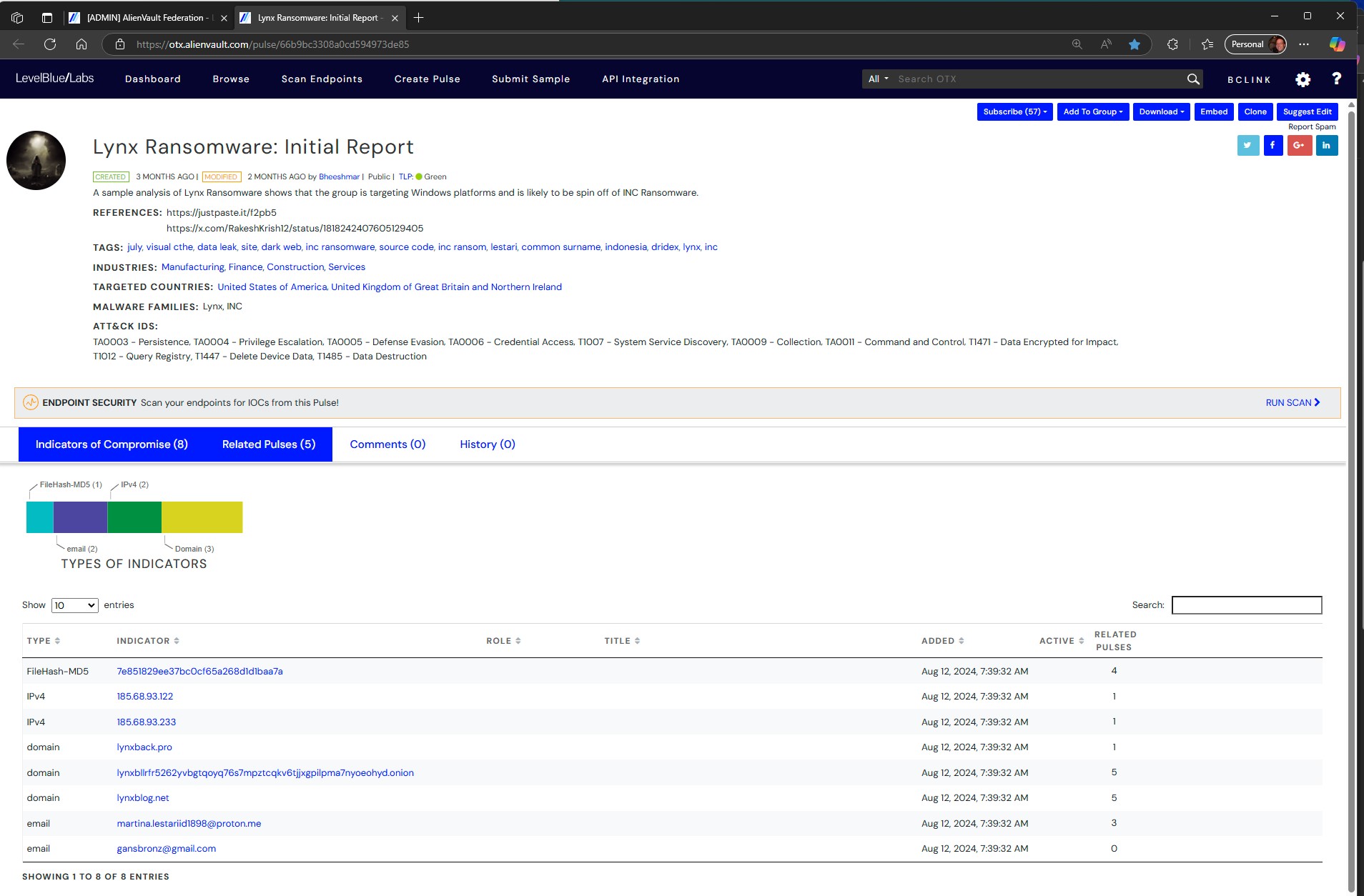
- IPv4: 80.66.83.49 – LevelBlue – Open Threat Exchange
- 466 E 35th St – Google Maps Domain registrar address for Lynx “hostile actor reporting site”.
- IPv4: 136.175.9.173 – LevelBlue – Open Threat Exchange
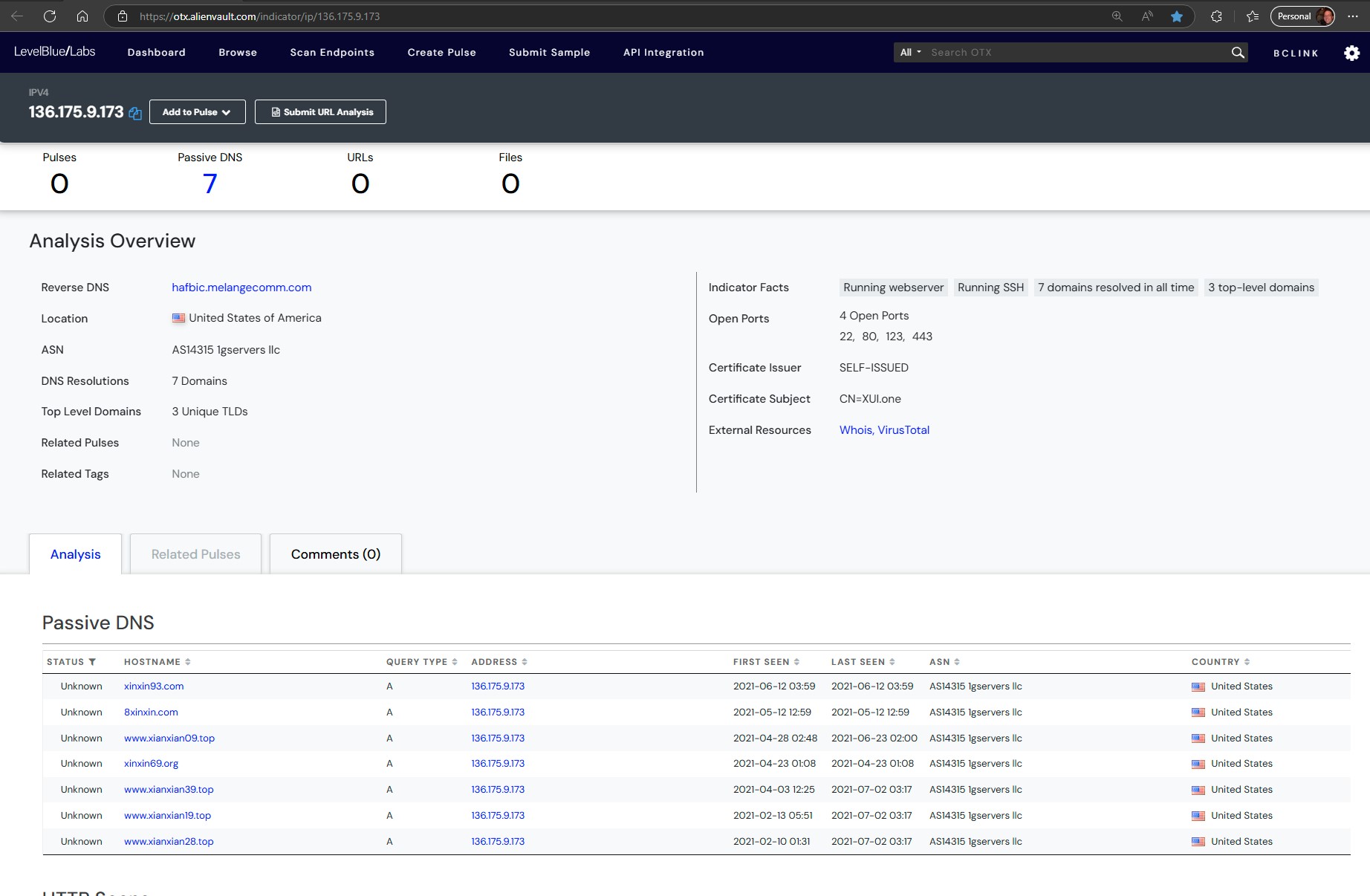
- (Cody -Osint)
- urlscan.io/api/v1/result/ea376d3f-2df5-4fb7-b13e-50914e232062/ API (hacker backend (exposed)) Safe as it is behind proxy Review the source for the page that’s hosting the “Disclosure”
- It’s proxied via URLScan.io so no worries on directly accessing it.
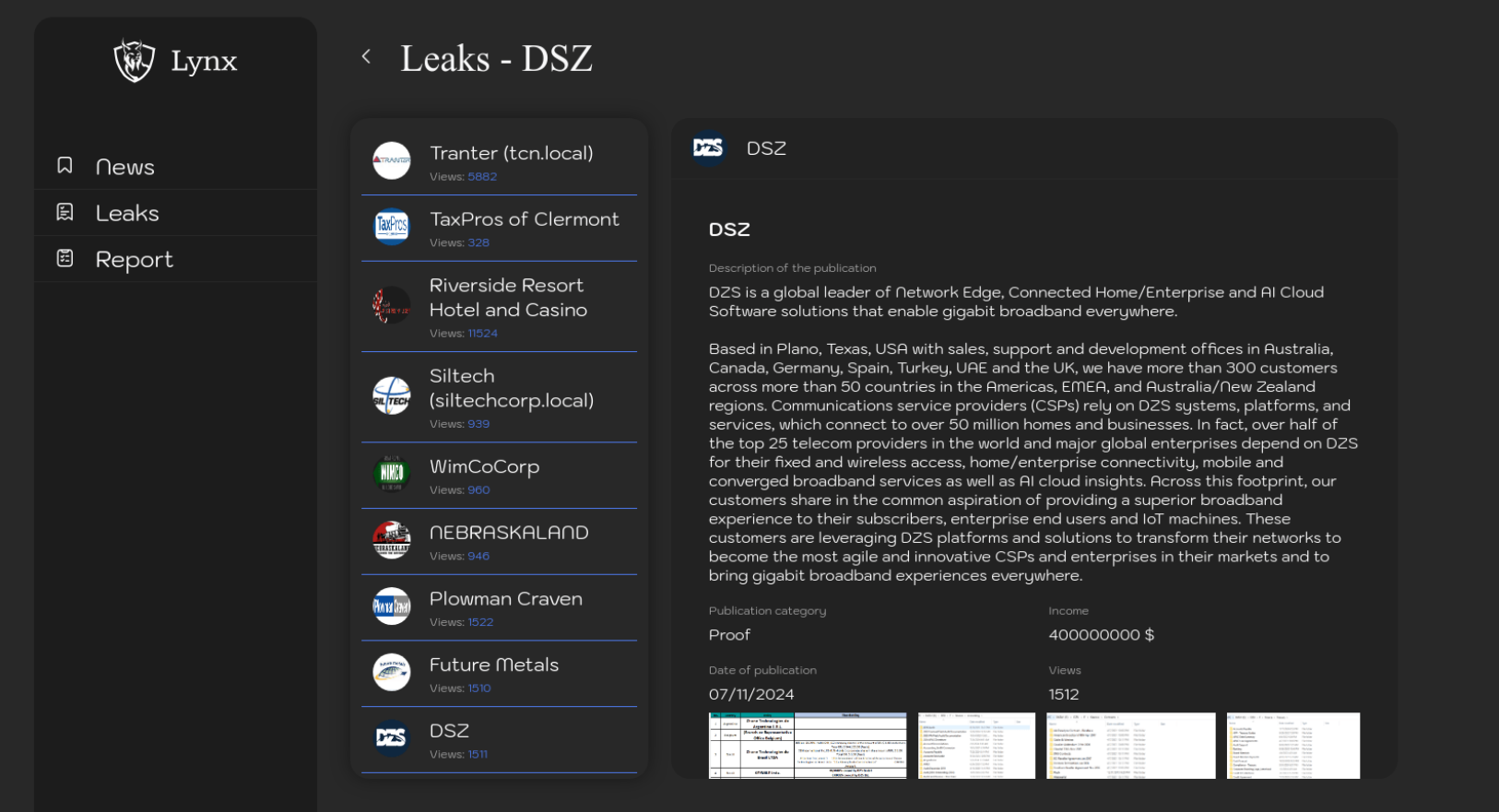
- https://justpaste.it/f2pb5https://x.com/RakeshKrish12/status/1818242407605129405 Link WAS up and now redacted, name is Rakesh Krish (found to be suspected cyber researcher)
Address for DNS in IMAGE. 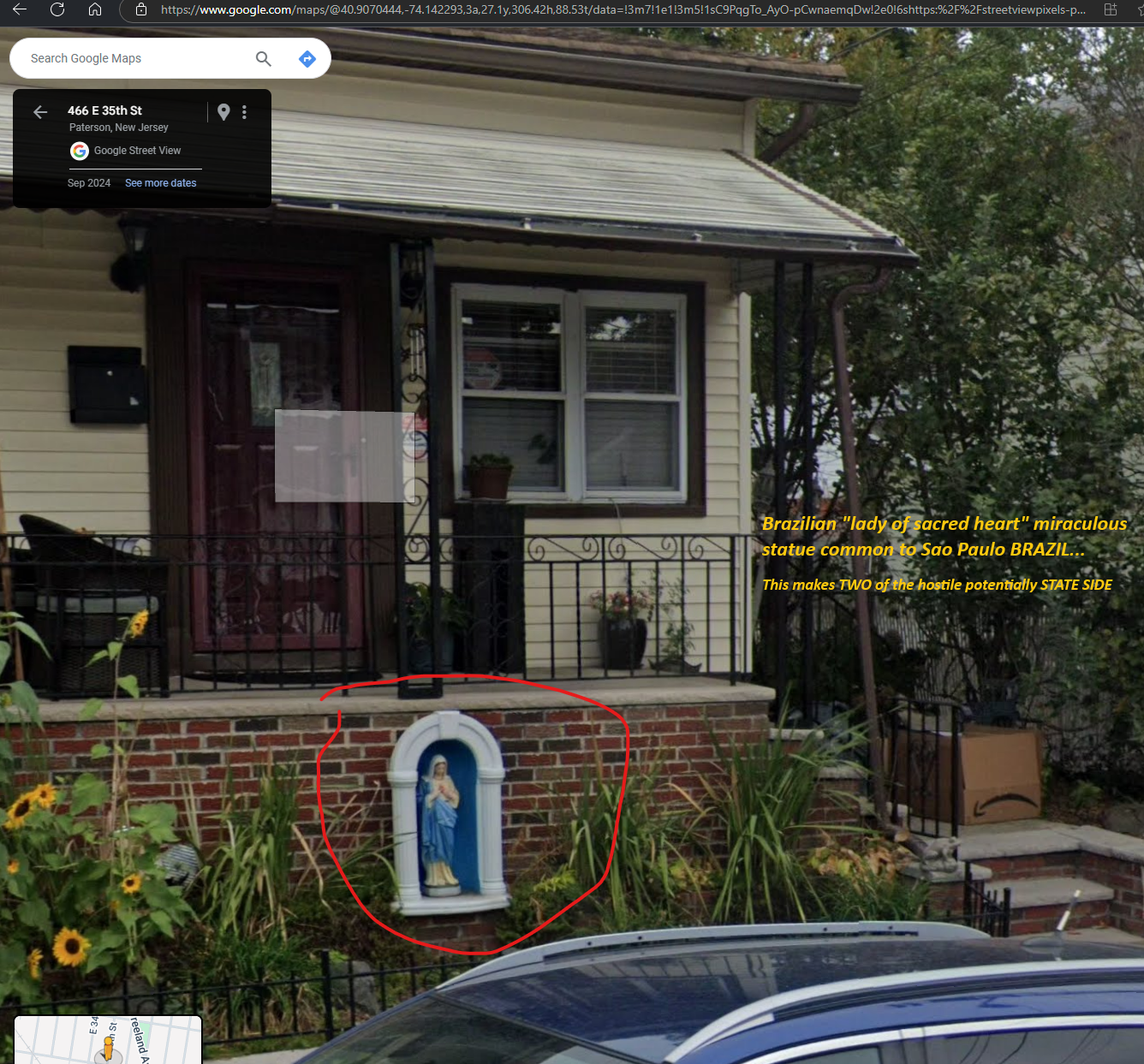
Image of “religion symbol” implies Portugal, Russia, Brazil, (potential Philippines) Immaculate heart of Mary or sacred heart of Mary. (specifics of crown and other segment origin)
Assumption (at current moment) Hostile Actors (2 in US) with RENTAL of the attack platform (in Russia), Hostile reporting site in Bulgaria, with US address for registered domain as shown.
Amazon will know ALL recipients at said address for shipped item seen in the photo, date of the Google earth “drive by” as reference.
Only INDIA reference found tied into this is
Analysis Overview – Likely was infected as part of the delivery pipe and not currently “hostile”.
Location  Delhi, India
Delhi, India
ASN AS209559 bcoolt creative media
DNS Resolutions 2 Domains
Top Level Domains 2 Unique TLDs
Related Pulses OTX User-Created Pulses (50)
Related Tags 24 Related Tags
portscan, LAMP,
malicious,
dionaea
More
Indicator Facts – OTX telemetry in last 7 days
Running webserver, Running SSH
2 domains resolved in all time – 2 top-level domains
Open Ports – 2 Open Ports 22, 80
External Resources
Passive DNS
| Status | Hostname | Query Type | Address | First Seen | Last Seen | ASN | Country |
|---|---|---|---|---|---|---|---|
| Unknown | p2.evanescentlabs.com | A | 80.66.83.49 | 2020-09-17 10:38 | 2020-09-27 10:27 | AS209559 bcoolt creative media |  India India |
| Unknown | seeds.wikiinfo.ru | A | 80.66.83.49 | 2019-05-29 07:09 | 2019-12-11 09:26 | AS209559 bcoolt creative media |  India India |
Lynx code snip 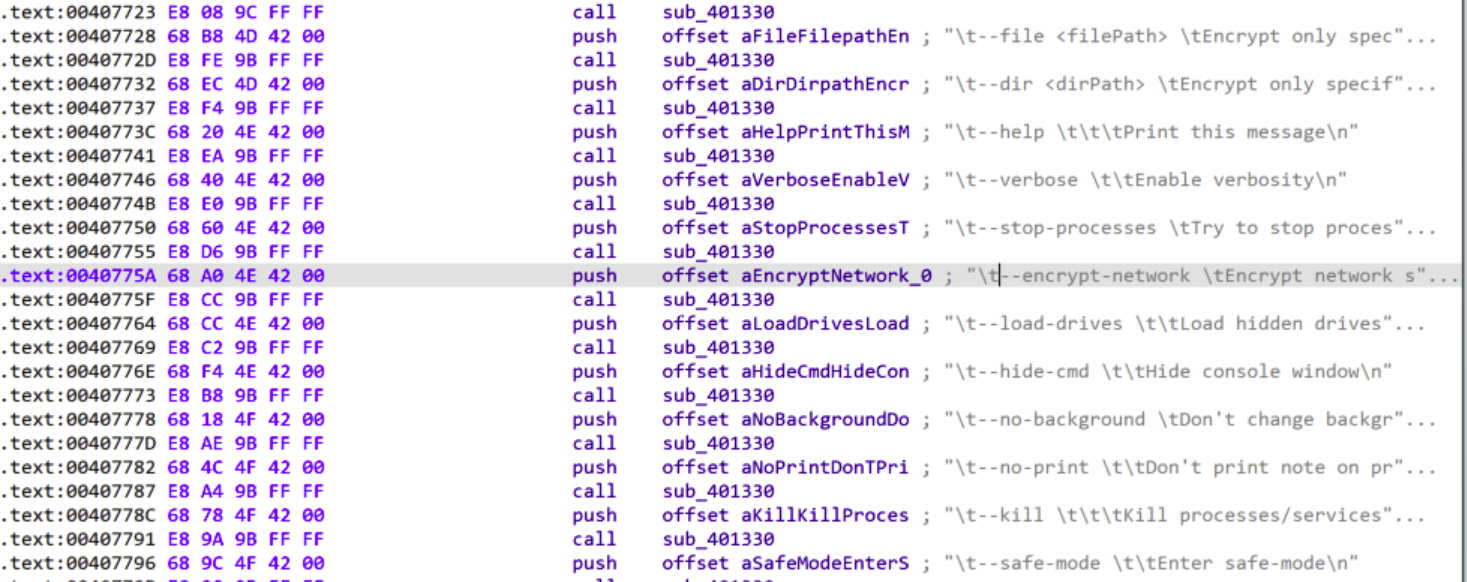
Code CAN crawl in context of user or escalated user to encrypt any mapped or network systems “vulnerable”!